A utilização de VRFs (Virtual Routing and Forwarding ou vpn-instance na linguagem HP) em Roteadores permite a criação de tabelas de roteamentos virtuais que trabalham de forma independente da tabela de roteamento “normal”, protegendo os processos de roteamento de cada cliente de forma individual.
Como nós explicamos anteriormente no post http://www.comutadores.com.br/roteamento-entre-vrfs-com-mp-bgp-em-roteadores-hp-h3c/ o rotemento entre VRFs (quando necessário) pode ser efetuado com a manipulação do route-targets (RT) com o processo MP-BGP ativo no Roteador.
Há também cenários em que é necessário a troca seletiva de prefixos de rede entre as tabelas de roteamento virtuais, escolhendo quais redes devem ser exportardas ou não entre as VRFs. Lembrando que os valores vpn-target (route-target) trabalham com as Extended community do BGP para troca de prefixos entre VRFs, é possível manipular o processo via route-policy (route-map), configurando a “comunidade estendida” para o prefixo e utilizando o comando export dentro da VRF.
Relembrando…
No diagrama abaixo há 2 VRFs já configuradas (com o processo MP-BGP ativo) e com seus respectivos prefixos.
Como os valores para import/export das VRFs não são os mesmos, não há roteamento entre as VRFs (cada VRF tem o seu roteamento isolado).

comutadores.com.br
# Roteamento Seletivo entre VRFs (1º exemplo)
!
ip vpn-instance Client_A
route-distinguisher 65000:1
vpn-target 65000:1 export-extcommunity
vpn-target 65000:1 import-extcommunity
#
ip vpn-instance Client_B
route-distinguisher 65000:2
vpn-target 65000:2 export-extcommunity
vpn-target 65000:2 import-extcommunity
#
!
interface Loopback1
ip address 1.1.1.1 255.255.255.255
!
bgp 65000
undo synchronization
#
ipv4-family vpn-instance Client_A
network 192.168.1.0
network 192.168.2.0
network 192.168.3.0
#
ipv4-family vpn-instance Client_B
network 172.16.1.0 255.255.255.0
network 172.16.2.0 255.255.255.0
network 172.16.3.0 255.255.255.0
#
#
ip route-static vpn-instance Client_A 192.168.1.0 255.255.255.0 NULL0
ip route-static vpn-instance Client_A 192.168.2.0 255.255.255.0 NULL0
ip route-static vpn-instance Client_A 192.168.3.0 255.255.255.0 NULL0
ip route-static vpn-instance Client_B 172.16.1.0 255.255.255.0 NULL0
ip route-static vpn-instance Client_B 172.16.2.0 255.255.255.0 NULL0
ip route-static vpn-instance Client_B 172.16.3.0 255.255.255.0 NULL0
#
#
[R1]display ip routing-table vpn-instance Client_A
Routing Tables: Client_A
Destinations : 5 Routes : 5
Destination/Mask Proto Pre Cost NextHop Interface
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
192.168.1.0/24 Static 60 0 0.0.0.0 NULL0
192.168.2.0/24 Static 60 0 0.0.0.0 NULL0
192.168.3.0/24 Static 60 0 0.0.0.0 NULL0
[R1]display ip routing-table vpn-instance Client_B
Routing Tables: Client_B
Destinations : 5 Routes : 5
Destination/Mask Proto Pre Cost NextHop Interface
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
172.16.1.0/24 Static 60 0 0.0.0.0 NULL0
172.16.2.0/24 Static 60 0 0.0.0.0 NULL0
172.16.3.0/24 Static 60 0 0.0.0.0 NULL0
No exemplo abaixo, caso manipulassemos o import/export, teríamos as 2 tabelas de roteamento compartilhadas…

# comutadores.com.br
# Roteamento Seletivo entre VRFs (2º exemplo)
!
#
ip vpn-instance Client_A
route-distinguisher 65000:1
vpn-target 65000:1 export-extcommunity
vpn-target 65000:1 65000:2 import-extcommunity
#
ip vpn-instance Client_B
route-distinguisher 65000:2
vpn-target 65000:2 export-extcommunity
vpn-target 65000:2 65000:1 import-extcommunity
#
!
interface Loopback1
ip address 1.1.1.1 255.255.255.255
!
bgp 65000
undo synchronization
#
ipv4-family vpn-instance Client_A
network 192.168.1.0
network 192.168.2.0
network 192.168.3.0
#
ipv4-family vpn-instance Client_B
network 172.16.1.0 255.255.255.0
network 172.16.2.0 255.255.255.0
network 172.16.3.0 255.255.255.0
#
#
ip route-static vpn-instance Client_A 192.168.1.0 255.255.255.0 NULL0
ip route-static vpn-instance Client_A 192.168.2.0 255.255.255.0 NULL0
ip route-static vpn-instance Client_A 192.168.3.0 255.255.255.0 NULL0
ip route-static vpn-instance Client_B 172.16.1.0 255.255.255.0 NULL0
ip route-static vpn-instance Client_B 172.16.2.0 255.255.255.0 NULL0
ip route-static vpn-instance Client_B 172.16.3.0 255.255.255.0 NULL0
#
#
[R1]display ip routing-table vpn-instance Client_A
Routing Tables: Client_A
Destinations : 8 Routes : 8
Destination/Mask Proto Pre Cost NextHop Interface
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
172.16.1.0/24 BGP 130 0 0.0.0.0 NULL0
172.16.2.0/24 BGP 130 0 0.0.0.0 NULL0
172.16.3.0/24 BGP 130 0 0.0.0.0 NULL0
192.168.1.0/24 Static 60 0 0.0.0.0 NULL0
192.168.2.0/24 Static 60 0 0.0.0.0 NULL0
192.168.3.0/24 Static 60 0 0.0.0.0 NULL0
[R1]display ip routing-table vpn-instance Client_B
Routing Tables: Client_B
Destinations : 8 Routes : 8
Destination/Mask Proto Pre Cost NextHop Interface
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
172.16.1.0/24 Static 60 0 0.0.0.0 NULL0
172.16.2.0/24 Static 60 0 0.0.0.0 NULL0
172.16.3.0/24 Static 60 0 0.0.0.0 NULL0
192.168.1.0/24 BGP 130 0 0.0.0.0 NULL0
192.168.2.0/24 BGP 130 0 0.0.0.0 NULL0
192.168.3.0/24 BGP 130 0 0.0.0.0 NULL0
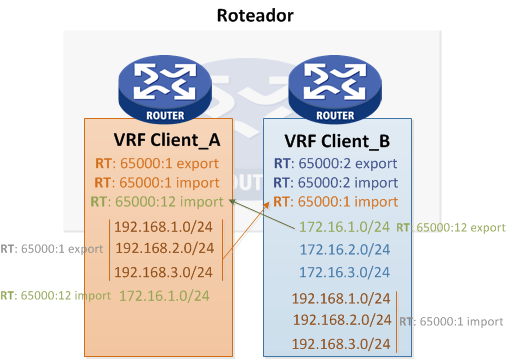
Mas imaginem que a VRF Client_B, por questões de segurança no roteamento, não precissasse ensinar os prefixos 172.16.2.0/24 e 172.16.3.0/24 para a VRF Client_A mas somente o prefixo 172.16.1.0/24…. Nesse caso precisaríamos configurar o roteamento seletivo para que a VRF Client_A aprenda somente os prefixos necessários.
Ja a VRF Client_A exportará todos os prefixos sem filtros para a Client_B
Utilizaremos no exemplo o valor da Extended Community 65000:12 para exportar o prefixo 172.16.1.0/24.
ip ip-prefix Client_B_prefixo index 5 permit 172.16.1.0 24
! Selecionando o prefixo via prefix-list
!
route-policy Client_B_export permit node 10
if-match ip-prefix Client_B_prefixo
apply extcommunity rt 65000:12 additive
#
! Configurando a community estendida via Route-map
!
ip vpn-instance Client_B
export route-policy Client_B_export
quit
! Configurando o export seletivo de prefixo
end
!
#
ip ip-prefix Client_B index 5 permit 172.16.1.0 24
#
route-policy Client_B permit node 10
if-match ip-prefix Client_B
apply extcommunity rt 65000:12 additive
#
ip vpn-instance Client_A
route-distinguisher 65000:1
vpn-target 65000:1 export-extcommunity
vpn-target 65000:1 65000:12 import-extcommunity
#
ip vpn-instance Client_B
route-distinguisher 65000:2
export route-policy Client_B
vpn-target 65000:2 export-extcommunity
vpn-target 65000:2 65000:1 import-extcommunity
#
!
interface Loopback1
ip address 1.1.1.1 255.255.255.255
!
bgp 65000
undo synchronization
#
ipv4-family vpn-instance Client_A
network 192.168.1.0
network 192.168.2.0
network 192.168.3.0
#
ipv4-family vpn-instance Client_B
network 172.16.1.0 255.255.255.0
network 172.16.2.0 255.255.255.0
network 172.16.3.0 255.255.255.0
#
#
ip route-static vpn-instance Client_A 192.168.1.0 255.255.255.0 NULL0
ip route-static vpn-instance Client_A 192.168.2.0 255.255.255.0 NULL0
ip route-static vpn-instance Client_A 192.168.3.0 255.255.255.0 NULL0
ip route-static vpn-instance Client_B 172.16.1.0 255.255.255.0 NULL0
ip route-static vpn-instance Client_B 172.16.2.0 255.255.255.0 NULL0
ip route-static vpn-instance Client_B 172.16.3.0 255.255.255.0 NULL0
#
#
[R1]disp ip routing-table vpn-instance Client_A
Routing Tables: Client_A
Destinations : 6 Routes : 6
Destination/Mask Proto Pre Cost NextHop Interface
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
172.16.1.0/24 BGP 130 0 0.0.0.0 NULL0
192.168.1.0/24 Static 60 0 0.0.0.0 NULL0
192.168.2.0/24 Static 60 0 0.0.0.0 NULL0
192.168.3.0/24 Static 60 0 0.0.0.0 NULL0
[R1]display ip routing-table vpn-instance Client_B
Routing Tables: Client_B
Destinations : 8 Routes : 8
Destination/Mask Proto Pre Cost NextHop Interface
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
172.16.1.0/24 Static 60 0 0.0.0.0 NULL0
172.16.2.0/24 Static 60 0 0.0.0.0 NULL0
172.16.3.0/24 Static 60 0 0.0.0.0 NULL0
192.168.1.0/24 BGP 130 0 0.0.0.0 NULL0
192.168.2.0/24 BGP 130 0 0.0.0.0 NULL0
192.168.3.0/24 BGP 130 0 0.0.0.0 NULL0
Obs: O mesmo controle pode ser feito para os prefixos de entrada, utilizando o “import map”
Dúvidas , deixe um comentário